Put a stop to malware, not to your Mac Keep your Mac safe with ClamXAV, the trusted anti-virus and malware scanner for macOS Free trial Buy now. Tick Mac security off your to-do list today The ClamXAV scanner efficiently heads off malware and viruses in the workplace and can help you to comply with critical audit requirements and guidelines. A file ending with tar.gz is a zipped (compressed) file. If you double click the file it should automatically unzip using the Mac's built-in software. Afterwards you should see your program in the same folder as the 'tarball' was. If your computer still has Mac OS X 10.6.8 to 10.9.5, you can use ClamXAV 2. Step 1 Find ClamXAV3.1.28690Installer.pkg in your Downloads Folder and double click it and follow the on-screen prompts to perform the installation. When asked for your admin name and password, these are the ones you use to log into your computer. ClamAV can be found in the apt repository. Run this command to install ClamAV: apt-get install clamav. If you need clamd, you may also want to run: apt-get install clamav-daemon. For the stable release, the packages are updated via the StableUpdates mechanism. Install ClamAV packages. To install ClamAV on CentOS 7, we need to install and enable EPEL.
I'm running ClamXav Sentry as 'launch agent' with ClamAV antivirus scanning engine of my own custom build.
I've tested for building ClamAV (from version 0.90.x to version 0.103.x) on Mac OS X 10.4 through macOS 11.0 Big Sur.
I'm running the latest stable release ClamAV 0.103.0 on macOS 11.0 Big Sur now.
ClamAV 0.103.0 is available on the Download page of ClamavNet, and the release note is here!
When you want to build ClamAV-devel from the Git sources, autotools are now requied.
For further information, see the following section:
'How to install ClamAV®-devel from the Git sources on macOS'.
This memorandum contains as below:
・ Memorandum 1: Building ClamAV 0.103.x on OS X 10.10 Yosemite through macOS 11.0 Big Sur
・ Memorandum 2: Building ClamAV 0.99.x on OS X 10.10, 10.11, 10.12 and macOS 10.13 High Sierra
・ Memorandum 3: Building ClamAV 0.98.7 on OS X 10.10 Yosemite and 10.11 El Capitan
・ Memorandum 4: Building ClamAV on Mac OS X 10.4 (Intel)
・ Memorandum 5: Building ClamAV on Mac OS X 10.4 (PPC)
・ Memorandum 6: Building ClamAV on Mac OS X 10.6 through OS X 10.9 Mavericks
・ Memorandum 7: Running clamd and freshclam as daemon
・ Memorandum 8: Running ClamXav Sentry as 'launch agent' on Mac OS X 10.6 and later…
・ Memorandum 9: Update ClamXav's own Virus Database and running RunFreshclam as daemon
・ Memorandum 10: Running ClamXAV version 2.18.x with B.Y.O. ClamAV antivirus scanning engine
・ Links…
1. Requirements to build ClamAV 0.103.x is very much the same as building ClamAV 0.102.x.
2. Requirements to build ClamAV 0.102.x are almost the same as building ClamAV 0.101.x. and ClamAV 0.100.x.
The differences are as follows:
LLVM current version is 10.0.x, though ClamAV 1.02.x supports only LLVM =< 3.6.x.
The ClamAV team is not maintaining repackaged LLVM now, and they may drop the repackaged LLVM entirely
and deprecate support for system-installed LLVM in favor of the bytecode interpreter.
So LLVM Libraries are not necessarily required to build ClamAV 0.102.x, I think.
I am now configuring ClamAV 0.102.x to disable LLVM as follows:
Of course you can configure ClamAV 0.102.x to enable LLVM as before:
3. Requirements to build ClamAV 0.102.x and ClamAV 0.101.x are almost same as before.
・ PCRE Libraries
・ OpenSSL Libraries
・ LLVM Libraries (Only when enabling LLVM)
4. Differences
Thus making ClamAV 0.100.x fails with an error:
To build ClamAV 0.100.x enabling the LLVM Just-In-Time compiler for executing bytecode signatures,
use this configuration:
or simply use this configuration to disable LLVM Just-In-Time compiler:
ClamAV 0.99.x contains major new features such as YARA rules, PCRE - Perl Compatible Regular Expressions and so on.
To support YARA and ClamAV logical signatures, the Perl Compatible Regular Expressions (PCRE) library is required.
If PCRE isn't installed on your system, you will get a warning message like this while running freshclam.
1. To ensure the PCRE library:
1) Install PCRE - Perl Compatible Regular Expressions.,
2) When compiling ClamAV 0.99.x, it fails with an error:
3) To avoid this failure, simply set CPPFLAGS:
4) And add this configuration option when configuring ClamAV: --with-pcre=/usr/local/pcre2.
2. To compile ClamAV 0.99.x on OS X 10.10 Yosemite or on OS X 10.11 El Capitan and macOS 10.12 Sierra,
1) LLVM Library is required on OS X 10.10 Yosemite.
2) LLVM Library and LibreSSL are required on OS X 10.11 El Capitan and macOS 10.12 Sierra.
Please readMemorandum 3 to learn more, and…
3) Install LLVM Library Binaries.
4) Install LibreSSL.
3. Configure ClamAV 0.99.x on OS X 10.10 Yosemite as follws:
4. Configure ClamAV 0.99.x on OS X 10.11 El Capitan and macOS 10.12 Sierra as follws:
Built-in LLVM of ClamAV 0.98.7 and 0.99.x are not compatible with GNU C++ on OS X 10.10 Yosemite and 10.11 El Capitan.
So ClamAV 0.98.7 and 0.99.x built on OS X 10.10 Yosemite or on OS X 10.11 El Capitan have major issues:
- Clamd crashes repeatedly throwing 'Segmentation Fault: 11'
- Clamscan also crashes and fails to scan…
- Freshclam fails to load new database logging:
These problems can be avoided by installing official LLVM.
Versions of LLVM beyond 3.6 seem not to be currently supported in ClamAV, so you should install LLVM 3.6.2.
1. Installing LLVM 3.6.2 Pre-built Binaries
2. To use LLVM installed into /usr/local as a system library instead of the ClamAV's built-in LLVM JIT,
add configuration option as following:
3. Configure ClamAV 0.98.7 on OS X 10.10.x Yosemite as follws:
Apple introduded a new security feature SIP: System Integrity Protection (rootless) to OS X 10.11 El Capitan, so in /usr directory
OS X 10.11 El Capitan has the different file composition from OS X 10.10 Yosemite.
While configuring ClamAV 0.98.7 on OS X 10.11 El Capitan, configuration fails with an error:
1. To solve this configuration issue, install LibreSSL.
 Setting search path:
Setting search path:You can confirm the installation:
2. But it's not still sufficient to succeed building.
Building fails with an error:
3. To succeed building ClamAV 0.98.7 on OS X 10.11 El Capitan, set CPPFLAGS:
4. Configure ClamAV 0.98.7 on OS X 10.11 El Capitan as follws:
5. Notes
In macOS 10.13 High Sierra, Apple seems to switch SSL libraries from OpenSSL 0.9.8zh to LibreSSL 2.2.7.
LibreSSL is a version of the TLS/crypto stack forked from OpenSSL in 2014.
And it is know to build and work on Mac OS X (tested with 10.8 and later).
So I have changed OpenSSL for LibreSSL to build ClamAV.
Now you can use LibreSSL 2.7.x (the latest stable release).
If you want to use OpenSSL as before, ClamAV 0.100.x is compatible with OpenSSL 1.1.1x,
so you can use OpenSSL 1.1.1x.
Clamav For Mac
If you use OpenSSL 1.1.1x to compile ClamAV 0.99.x, add more this configuration.
In last update, Clam AntiVirus developer team introduced JIT compiler to ClamAV® 0.96.
Apple gcc (version: 4.0.1 build: 5370) in Mac OS X 10.4 (aka Tiger) failed to build ClamAV 0.96.x and 0.98.x with JITcompiled in.
With a brief struggle I found a good solution that I will tell you here.
1) First, install LLVM (Low Level Virtual Machine) and LLVM-GCC 4.2 Front End.
2) Second, add this configuration option: --enable-llvm.
Then you can build ClamAV 0.96.x and 0.98.x with JIT compiled in and use new features included in anti-virus toolkit.
Install LLVM (Low Level Virtual Machine) and LLVM-GCC 4.2 Front End
1. Installing LLVM-GCC 4.2 Front End Binaries
2. Setting search path
3. Installing LLVM 2.3
Install MacPorts and the packages
1. Installing MacPorts
Ensure it's up to date by running:
2. Installing the packages: bzip2
3. Maintaining MacPorts and installed packages
Compile ClamAV 0.98.x and Install
1. Modify /shared/output.c & output.h to avoid compiling error. (Only needed for compiling ClamAV 0.98.1)
2. ./configure (version 0.98 and 0.98.1)
3. ./configure (version 0.98.3 or later)
4. Make, make check and install ClamAV
To compile ClamAV 0.96.3 or later, bzip2 (Version 1.0.6) that fixes CVE-2010-0405 is required.
Mac OS X has bzip2 (Version 1.0.5) built-inand it is outdated, so you get WARNING as follows while running configuration command.
To solve this problem on Mac OS X 10.4, you can install bzip2 (Version 1.0.6) using MacPorts and add this configuration option:
export LDFLAGS='-L/opt/local/lib' as follows.
Apple has patched the CVE-2010-0405 bug on Mac OS X 10.6.7 but not on Mac OS X 10.4.11.
To compile ClamAV 0.98.3 or later, OpenSSL (Version 0.98y or above including the X509_VERIFY_PARAM function) is required.
Mac OS X 10.4 has OpenSSL 0.9.7l built-in and MacPorts fails to build OpenSSL, so you have to install OpenSSL 0.9.8zh.
1. Install OpenSSL 0.9.8zh
2. Setting search path
Compile ClamAV 0.99.x and Install
To compile ClamAV 0.99.x on Mac OS X 10.4, in addition to installing LLVM Front End, MacPorts, bzip2 and OpenSSL the PCRE library is required as pointed out above.

1. Install PCRE - Perl Compatible Regular Expressions.
2. ./configure
3. Make, make check and install ClamAV
PPC users have to install LLVM-GCC 4.2 Front End Binaries for PPC and configure ClamAV 0.96.x and 0.98.x with different configuration.
Install LLVM (Low Level Virtual Machine) and LLVM-GCC 4.2 Front End
1. Installing LLVM-GCC 4.2 Front End Binaries
2. Setting search path
3. Installing LLVM 2.3
Install MacPorts and the packages
1. Installing MacPorts
Ensure it's up to date by running:
2. Installing the packages: bzip2
3. Maintaining MacPorts and installed packages
Compile ClamAV 0.98.x and Install
1. Modify /shared/output.c & output.h to avoid compiling error. (Only needed for compiling ClamAV 0.98.x)
2. ./configure
3. Make, make check and install ClamAV
GNU C++ and bzip2 (Version 1.0.6) are installed on Mac OS X and later, so you can simply build ClamAV 0.96.x and 0.98.x with JIT compiled in and use new features included in anti-virus toolkit.
1. On Mac OS X 10.7, after installing Xcode 4.3 in /Applications, you should install the Command Line Tools:developer.apple.com. and
2. Run these commands to make sure that everything is pointed in the right place.
Compile ClamAV 0.98.x and Install
1. ./configure
2. Make, make check and install ClamAV
Compile ClamAV 0.99.x and Install
1. To compile ClamAV 0.99.x, the PCRE library is required as pointed out above.
2. ./configure
3. Make, make check and install ClamAV
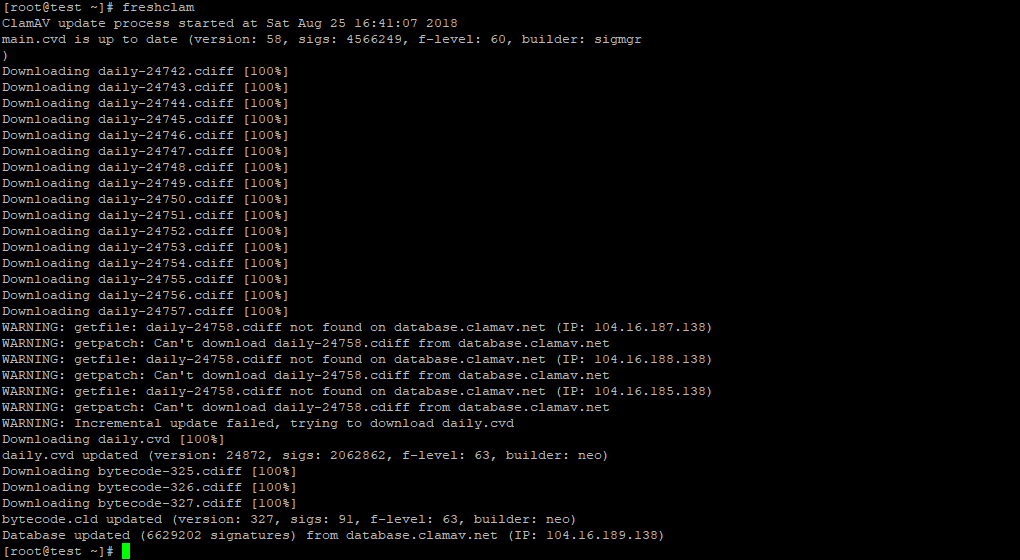
1. I'm running clamd and freshclam as 'launch daemon' managed by:
/Library/LaunchDaemons/org.clamav.freshclam.plist
 2. Edit clamd.conf and freshclam.conf for using ' daemons'.
2. Edit clamd.conf and freshclam.conf for using ' daemons'.3. Set appropriate permissions for ClamXav and ClamXav Sentry.
4. Notes
uncheck 'Update virus definitions on launch' of ClamXav's 'General Preferences' section.
Updates of virus definitions gets executed automatically by 'freshclam daemon'.
1. When running ClamXav Sentry as 'launch agent', ClamXav Sentry keeps alive.
I'm running ClamXav Sentry as 'launch agent' managed by ~/Library/LaunchAgents/org.clamXavSentry.plist
2. On Yosemite and El Capitan, I'm using this org.clamXavSentry.plist file to avoid ClamXav Sentry's annoying error:
3. Notes
uncheck 'Launch ClamXav Sentry when you log in to this computer' of 'ClamXav Sentry Preferences' section.
ClamXav Sentry automatically launches and keeps alive by 'launch agent' when logging in.
CFBundleExecutable name 'ClamXavSentry' was replaced by 'ClamXav Sentry' in ClamXav 2.7.x.
So you should replace 'ClamXavSentry' with 'ClamXav Sentry' in org.clamXavSentry.plist.
If you are running clamd as 'launch daemon' and running ClamXav Sentry 3.x as 'launch agent',
use this hidden preference setting:
And if you are running clamd as 'launch daemon' and running ClamXav Sentry 3.5.x as 'launch agent',
use this hidden preference setting:
1. Now ClamXav and ClamXav Sentry use combined official and its own virus database as below:
2. To get and update ClamXav Virus Database,
and place it into
ClamXav 2.8.9.4 requires empty file called 0.99.1_update_4 inside /usr/local/clamXav.
3. When you launch ClamXav 2.8.9.1 and update virus definitions, ClamXav logs follwing error:
For details, see 'Bug 11455 – [Clamav-devel] Patch to force freshclam download progress meter'.
To solve this issue, get and apply 'freshclam_show-progress.patch' before you build ClamAV 0.99.0.
--------
The patch has been checked in ClamAV 0.99.1 repository, so no need for patching to build ClamAV 0.99.1.
1. I'm now running RunFreshclam as 'daemon' instead of freshclam daemon managed by:
/Library/LaunchDaemons/com.clamXav.runfreshclam.plist
Clamav For Linux
2. Edit freshclam.conf for using RunFreshclam ' daemons'.3. Set appropriate permissions for RunFreshclam (ClamXav version =< 2.8.x).
Notes:
As concerns appropriate permissions on ClamXav 2.9.x, see described below.
4. Checking and updating virus definitions:
'RunFreshclam' automatically (at regular time intervals, e.g. every 30minutes or every 1 hour as you set) executes checking and updating both ClamXav's own virus definitions and official ClamAV® virus definitions, so you need not run 'freshclam daemon'.
An example of freshclam.log:
Clamav Windows
1. ClamXav has a new engine install and uninstall mechanism since version 2.9.
When you fail to satisfy the requirements, ClamXav tries to repair /usr/local/clamXav, and all files and folders are changed to its own official engine.
To satisfy the requirements, the following files are needed at the very least in addition to B.Y.O. ClamAV files:
2. Steps to satisfy the requirements for ClamXAV Version 2.19.3 (3715):
1) make empty file called 0.100.1_update_08 inside /usr/local/clamXav/
2) extract gfslogger and RunFreshclam from ClamXAV.app/Contents/Resources/clamavEngineInstaller.pkg
3) place those files into appropriate directory:
First run RunFreshclam completely, then you can place them at /usr/local/clamXav/share/clamav/ as follws:
5) Set appropriate permissions at /usr/local/clamXav for ClamXAV 2.19.x.
3. Now you can run ClamXAV Sentry 3.19.x as 'launch agent' and run RunFreshclam as 'launch daemon' with no issues.
An example of freshclam.log:
4. Important Notes
If you keep using B.Y.O. Engine, do that on your own risk.
Now ClamXAV 3 is available, thus ClamXAV 2 will not receive malware database updatesbeyond 31st October 2018.
ClamAV on Mac with Kerio MailServer
© May 2019 Anthony Lawrence
I downloaded ClamAV source from https://www.clamav.net. A simple ./configure; make; make install in the source directory was all that was required (thogh you do have to install the Xcode Tools from your install cd if you haven't already).
Well, gosh, that was easy. Now what?
Well, that depends on what you plan to do with it. If you only plan to scan files on your drives, there's nothing else you need.If you are planning to use the supplied 'clamav-milter' (see Sendmail Milters),you need to add the milter to your mail configuration (and you would have needed to run './configure --enable-milter' before compiling).See clamav-milter(link dead, sorry)for very basic instructions on adding this milter to sendmail.
In my case, I wanted to use it with Kerio Mailserver.
Kerio MailServer is able to work with several virus scanning engines. The preferred primary is McAfee, but (depending on your OS platform) other plugins can be used. As of version 6.1, they introduced the ability to do dual scanning, which allows each message to be scanned by two different AV products (one must be their McAfee option). Dual scanning can increase the chances of detecting viri.
Now with the 6.2 release (available in beta as I write this), ClamAV support has been added and can be used either as the stand-alone scanner or as the secondary to McAfee.
To use ClamAV with Kerio MailServer you need to get /usr/local/sbin/clamd running on the Mac (basically the same procedure applys to Linux) . That's going to requre editing (with sudo) two configuration files: /usr/local/etc/clamd.conf and /usr/local/etc/freshclam.conf
ClamAV forces you to at least comment out the 'Example' line from these files:
# Comment or remove the line below.
Example
For freshclam.conf that may be all you want or need to do, but at least this made you aware that the file exists and that you do have options to control freshclam. Freshclam is the program that updates Clamav's virus database, so you probably want to set it to run periodically with cron.
You'll need to do a little more with /usr/local/etc/clamd.conf. In addition to commenting out the 'Example', you need to set 'TCPSocket 3310' and you probably want to set 'TCPAddr 127.0.0.1' unless Kerio is running on a different machine than ClamAV.
With these set, you can start /usr/local/etc/clamd. After starting it, you should see it listening on port 3310:
Install Clamav On Mac
$ sudo /usr/local/sbin/clamd
$ sudo lsof -i:3310
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
clamd 18975 root 0u IPv4 0x2f92e88 0t0 TCP localhost:dyna-access (LISTEN)
Of course you'll want clamd starting up on reboot. It would be best to handle that through Launchd but you could also just add it to /etc/rc if you want. Launchd gives you more control to restart if necessary.
Kerio automatically tests Clam with an EICAR file but you can send the same pattern to a local user if you aren't the trusting sort. I tested, and found the expected entry in the Kerio Security Log:
I'm glad to see this support added to Kerio. I think it would have been better if they had implemented milter support because that would allow even more options for Kerio users, but this is a welcome addition.
Got something to add? Send me email.
(OLDER) <- More Stuff -> (NEWER) (NEWEST)
Printer Friendly Version
-> -> ClamAV on Mac
Clamav Mac Os
Inexpensive and informative Apple related e-books:
El Capitan: A Take Control Crash Course
Take Control of Numbers
iOS 10: A Take Control Crash Course
Take Control of IOS 11
Photos: A Take Control Crash Course